Disabling TLS 1.0 and TLS 1.1
Tuesday 13th March 2018
I recently received a security report to my HackerOne program by retr0, who suggested that I disable TLS 1.0 on my web server.
At first I was reluctant as this breaks compatibility with many older browsers, however after monitoring the TLS protocol versions in use by users, I've now disabled both TLS 1.0 and TLS 1.1, meaning that only TLS 1.2 can be used.
Thanks again to retr0 for raising this!
Skip to Section:
Disabling TLS 1.0 and TLS 1.1 ┣━━ What is wrong with TLS 1.0 and TLS 1.1? ┣━━ Checking for TLS 1.0 and TLS 1.1 Support ┣━━ Browser Compatibility ┣━━ Logging TLS Protocol Versions in Use in Apache ┗━━ Disabling TLS 1.0 and TLS 1.1 in Apache
What is wrong with TLS 1.0 and TLS 1.1?
These versions of the Transport Layer Security (TLS) protocol were first defined in January 1999 (RFC2246) and April 2006 (RFC4346) respectively, and since then various issues and vulnerabilities have been discovered.
However, there are currently no major vulnerabilities affecting TLS 1.0 and TLS 1.1 when using the latest browsers and server-side implementations. The notable issues with these protocols are found in certain TLS implementations, rather than being fundamental protocol flaws. This means that simply updating your TLS implementation (eg: OpenSSL, GnuTLS) as well as your browser will fix the issues.
RFC7457 provides summaries on some of these attacks, and there is an article by Acunetix that also provides some useful details.
However, older versions of TLS have begun to be phased out across the internet. Many large sites such as GitHub and NIST have already disabled older versions, while many more organisations have plans in place to disable them in the near future. Just yesterday as I was writing this, Cloudflare announced that they are going to be deprecating TLS 1.0 and TLS 1.1 on their API and dashboard come 4th June 2018.
It is also important to note that the new PCI DSS requirements state that TLS 1.0 must be disabled by 30th June 2018 in order to remain compliant.
Checking for TLS 1.0 and TLS 1.1 Support
You can easily check whether your server supports TLS 1.0 and TLS 1.1 using Nmap. This is available in the default repositories on most Linux distributions, and is also available on BSD, macOS and Windows.
Nmap has a built-in script to enumerate the available ciphers and protocols:
$ nmap -p 443 --script ssl-enum-ciphers jamieweb.net
This will output all of the supported SSL/TLS protocol versions and ciphers.
Alternatively, you can use the Qualys SSLLabs Scanner.
Browser Compatibility
The main downside to disabling TLS 1.0 and TLS 1.1 is that you lose support for some older browsers.
TLS 1.0 is supported in essentially all web browsers since the early 2000's.
TLS 1.1 support was added in:
- Chrome 22: 31st July 2012
- Firefox 24*: 6th August 2013
- Safari 7: 27th October 2013
- iOS 5: 7th March 2012
- Opera 12.1: 5th November 2012
- Internet Explorer 11*: 17th October 2013
- Microsoft Edge: All Versions Supported
...and TLS 1.2 support was added in:
- Chrome 30: 20th August 2013
- Firefox 27*: 4th Febuary 2014
- Safari 7: 22nd October 2013
- iOS 5: 7th March 2012
- Opera 17*: 7th October 2013
- Internet Explorer 11*: 17th October 2013
- Microsoft Edge: All Versions Supported
*: Some browsers supported TLS 1.1 and TLS 1.2 in versions earlier than those stated above, but it was disabled by default. If a legitimate user is still using such a dated browser, it is unlikely that they would have manually enabled support for the newer TLS protocol versions. One possible exeption to this is a managed organisation environment where out of date browsers are used, but support for the newer protocols is enabled via a centralised management tool such as Puppet.
Browser Compatibility Information Source: caniuse.com - Please see their fantastic browser compatibility reference pages on TLS 1.1 and TLS 1.2.
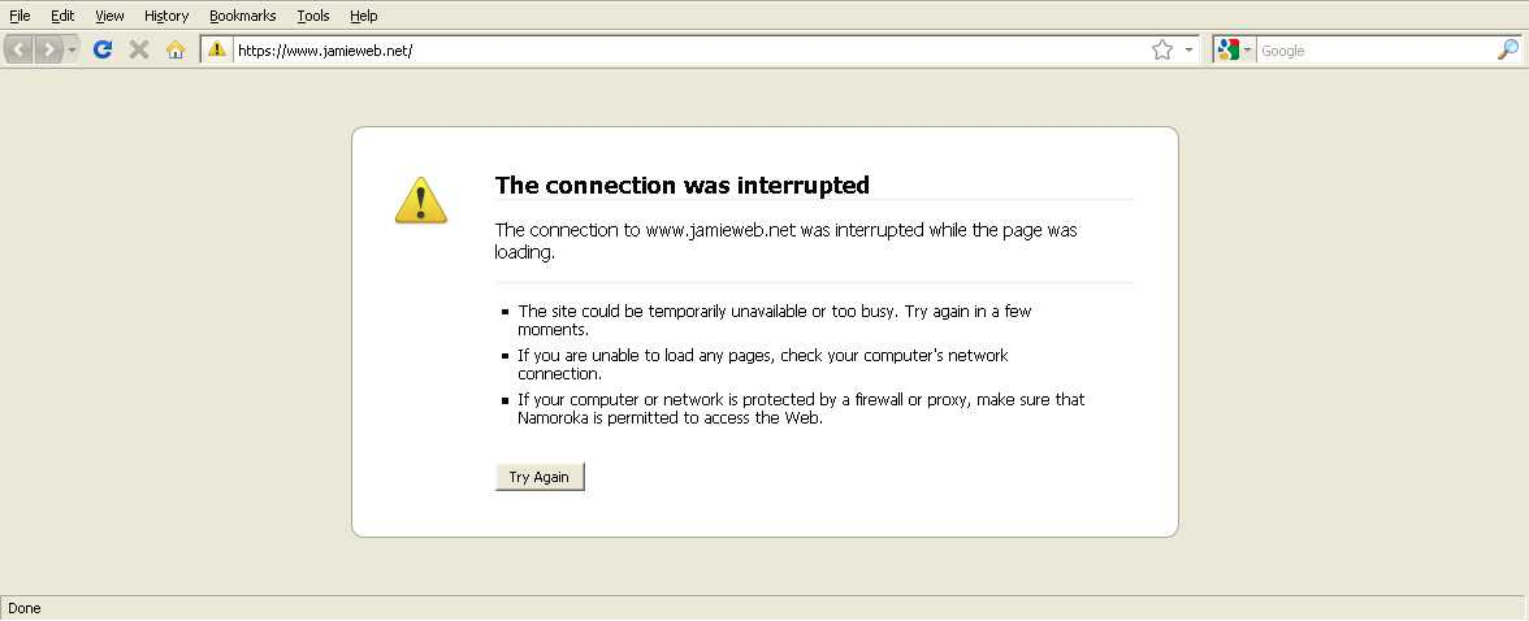
Connecting to jamieweb.net using Firefox 3.6, which does not support TLS 1.1 or TLS 1.2. Original screenshot generated by urlquery.net.
Losing compatibility with most of these browsers is not a major problem since their usage shares are now extremely low. The only one that looks slightly concerning is Internet Explorer 10, since many unpatched versions of Windows 7 still use this browser, however according to the stats above its usage share is only 0.12%.
Logging TLS Protocol Versions in Use in Apache
Before disabling TLS 1.0 and TLS 1.1, it is important to assess the impact that this could have on your users. The best way to do this is by monitoring the web server log files directly, as this gives the most raw results.
In Apache, this is extremely easy to configure using the CustomLog directive. Add the following to the virtual host that you want to monitor, and the TLS protocol version will be logged for all requests:
CustomLog ${APACHE_LOG_DIR}/tls.log "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x"
You can also optionally log the user agent string in order to help identify which client software is still using older TLS protocol versions:
CustomLog ${APACHE_LOG_DIR}/tls.log "%t %h %{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%{User-agent}i\""
As far as I know, this configuration does not work when specified in a global configuration file, it has to be directly in the virtual host configuration. I'm not sure why this is, but when defining the CustomLog globally, it doesn't seem to log the TLS information correctly even when there are definitely TLS requests reaching the server.
Leave this running for a while in order to get a good set of sample data.
You can then check the total number of requests, as well as the number of requests that did not use TLSv1.2:
$ wc -l tls.log $ grep -v "TLSv1.2" tls.log | wc -l
Using the results from the above commands, you can calculate the percentage of requests that did not use TLSv1.2.
I left my log running for around 20 hours, and in total there were just over 100,000 TLS requests. Out of these, only 0.078% were not using TLS 1.2.

A graph showing the number of TLS connections per protocol version during the 20 hour monitoring period.
As you can see above, the columns for TLS 1.0 and TLS 1.1 are barely even visible.
It is important to note that the data for my site is probably very biased, as this is a technical site with likely technical visitors. However that is OK, as I wanted to know the potential impact on my site, rather than on the internet as a whole.
Disabling TLS 1.0 and TLS 1.1 in Apache
In order to specify which SSL/TLS protocol versions you want to use in Apache, the SSLProtocol directive must be used. In order to only allow TLS 1.2, simply use:
SSLProtocol TLSv1.2
You can also specify multiple versions, including using the all shortcut:
SSLProtocol all -SSLv2 -SSLv3
Please see the Apache documentation for full details.
Test the server configuration with apachectl configtest, then reload the server with service apache2 reload.
You should then re-test your server in order to make sure that the configuration was correct. Also, if you enabled the TLS protocol version logging, don't forget to disable it as the log files can get quite large.
An alternative to hard-disabling these protocols is to redirect them to a page suggesting that the user upgrade their browser. This can be achieved in Apache using mod_rewrite:
RewriteEngine on
RewriteCond %{SSL:SSL_PROTOCOL} ^TLSv1.0$
RewriteCond %{SSL:SSL_PROTOCOL} ^TLSv1.1$
RewriteRule ^ https://www.jamieweb.net/tls-unsupported.php [END,R=302]
...although this does require you to keep the insecure protocols enabled in order to allow the connection for the redirect.